Blog Posts
Aeternum C2: The Takedown Resistant Botnet Using Blockchain

Cybersecurity researchers have revealed details about a new botnet loader called Aeternum C2, which uses a blockchain-based command and control (C2) infrastructure to resist takedown efforts. Instead of relying on traditional servers or domains, Aeternum stores its instructions on the public …
Analysis of a Multi-Stage Infection Chain: From Obfuscated JScript to Remcos RAT
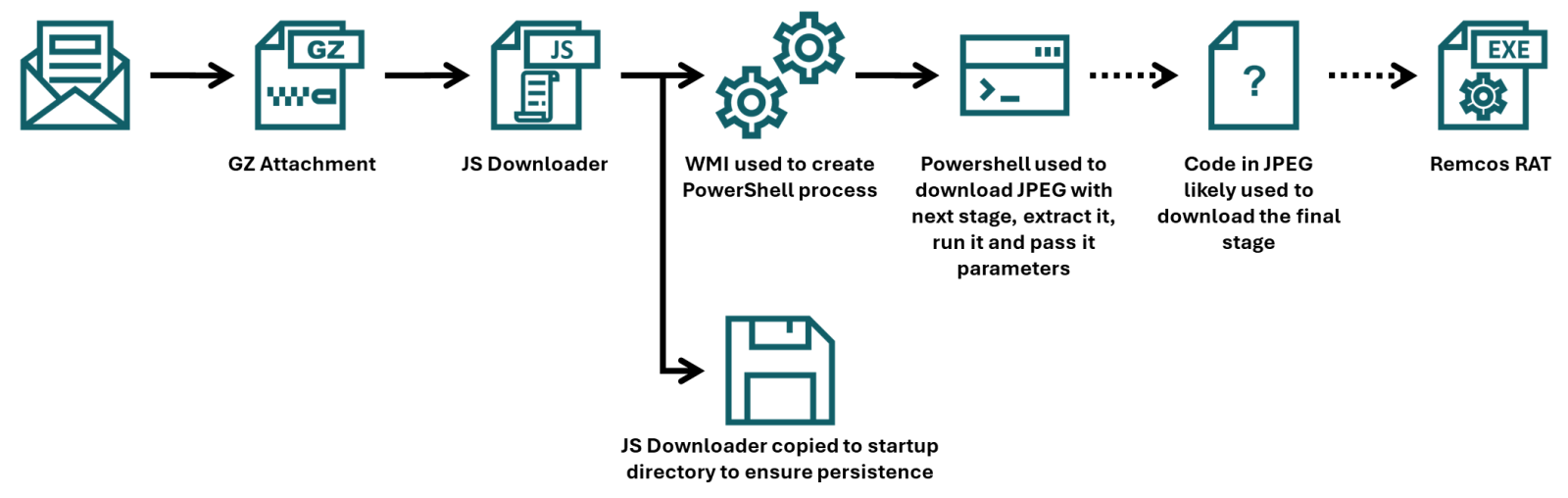
This article presents a detailed analysis of a recent malware campaign that uses advanced obfuscation techniques to evade detection. The infection chain begins with a JScript script attached to a phishing email and culminates with the download of Remcos RAT. The analysis focuses on the obfuscation …
NDR and EDR: Necessary Defenses against the Evolution of AI Threats

Cybersecurity faces a constant challenge: innovation from adversaries. The rise of offensive artificial intelligence (AI) is transforming attack strategies, making them harder to detect. Threat actors use large language models (LLMs) to hide code and generate malicious scripts on the fly. These …
Cloudflare details 25-minute BGP route leak incident

Cloudflare has shared details about a recent Border Gateway Protocol (BGP) route leak incident that affected IPv6 traffic for 25 minutes. The incident caused significant congestion, packet loss, and the drop of approximately 12 Gbps of traffic, impacting external networks beyond Cloudflare’s …
Fortinet Confirms Exploitation of FortiCloud SSO Authentication Bypass Vulnerability on Patched Devices

Fortinet has confirmed that it is working to fully fix a FortiCloud SSO authentication bypass vulnerability, following reports of new exploit activity on firewalls that had already been fully patched.
Discovery of New Attack Route
Carl Windsor, CISO of Fortinet, reported that cases of exploitation …
Microsoft releases emergency patches for Office zero-day vulnerability

Microsoft has released emergency out-of-band security updates to patch a high-severity zero-day vulnerability in Microsoft Office that is being actively exploited in attacks.
The vulnerability, tracked as CVE-2026-21509, is a security feature bypass that affects multiple versions of Office, …
New Cyber Espionage Campaign Targets Indian Users with Multi-Stage Blackmoon Backdoor

Cybersecurity researchers have uncovered an ongoing cyber espionage campaign specifically targeting users in India. The attack utilizes a multi-stage backdoor and leverages sophisticated evasion techniques to achieve persistent access and data exfiltration from compromised systems.
Initial Attack …
New Dual-Vector Campaign Uses Stolen Credentials and Legitimate RMM Software

Cybersecurity researchers have revealed details of a new dual-vector attack campaign that leverages stolen credentials to deploy legitimate Remote Monitoring and Management (RMM) software. The goal is to establish persistent remote access to the compromised hosts.
According to researchers at …
PeckBirdy: A Versatile Script Framework Used by China-Aligned APT Groups

This report details two threat campaigns using the PeckBirdy JavaScript framework, attributed to China-aligned advanced persistent threat (APT) actors. The campaigns, temporarily named SHADOW-VOID-044 and SHADOW-EARTH-045, demonstrate the increasing sophistication and adaptability of these groups. …
Risks of AI chatbots for children and how to mitigate them

The use of artificial intelligence (AI) chatbots has become widespread rapidly, with platforms like ChatGPT reaching hundreds of millions of users, many of them young people. A 2025 UK study revealed that almost two-thirds (64%) of children use these tools. Despite its popularity, the frequent use …
Sandworm attacks Poland's electrical system with new DynoWiper malware

The Russian state-linked Sandworm hacking group has been identified as responsible for what is described as the “largest cyberattack” targeting Poland’s power system in the last week of December 2025. Although the attack was detected and neutralized without causing any disruption, …
ShinyHunters claims 2 million Crunchbase records; the company confirms the breach

Crunchbase has confirmed a cybersecurity incident following claims by the cybercriminal group ShinyHunters, which claims to have stolen more than 2 million personal records from its systems.
ShinyHunters leaked a 402MB zip file on its Tor website, stating that the data release was due to a failed …
Ingram Micro reveals data breach after ransomware attack in July 2025

Ingram Micro Suffers Data Breach Due to Ransomware Attack
Information technology giant Ingram Micro has confirmed a data breach affecting more than 42,000 people, the result of a ransomware attack detected in July 2025. The company, a global B2B service provider and technology distributor with net …
Malicious Chrome Extensions Steal ChatGPT and DeepSeek Conversations

Cybersecurity researchers have discovered two new malicious extensions in the Chrome Web Store designed to exfiltrate OpenAI ChatGPT and DeepSeek conversations, along with browsing data, to servers under the attackers’ control. This type of attack, which uses browser extensions to stealthily …
Palo Alto Networks Security Update: Denial of Service Vulnerability in GlobalProtect

Palo Alto Networks has released a major security update to address a high severity vulnerability affecting its GlobalProtect Gateway and Portal software. The company has confirmed the existence of a proof-of-concept (PoC) exploit for this flaw, underscoring the urgency of patching.
Vulnerability …
CERT-UA Details New Cyber Attacks Against Ukrainian Defense Forces

Ukraine’s Computer Emergency Response Team (CERT-UA) has revealed details of a series of new cyberattacks targeting its defense forces and state institutions. These attacks, which took place between October and December 2025, involve various intrusion techniques and several malware families, …
Threat actor claims the theft of full customer data from Spanish energy firm Endesa

Endesa Confirms Security Incident Following Threat Actor Statement
Spanish energy company Endesa has confirmed a security incident that resulted in unauthorized access to its trading platform, compromising customer data. Endesa is the largest electricity supplier in Spain, serving more than 10 …
Veeam releases security patches to fix multiple critical vulnerabilities, including RCE

Veeam has released a series of critical security updates to its Backup & Replication software, addressing multiple flaws, including a vulnerability classified as “critical” that could lead to remote code execution (RCE).
Critical Remote Code Execution (RCE) Vulnerability
The most …
IBM API Connect: Critical Security Flaw Allows Remote Access

IBM has disclosed details about a critical security flaw in its API Connect product that could allow remote attackers to gain unauthorized access to the application.
Vulnerability Details
The vulnerability, identified as CVE-2025-13915, has received a score of 9.8 out of 10.0 in the CVSS rating …
Critical Vulnerability Alert in SmarterTools SmarterMail: Remote Code Execution without Authentication

Critical Vulnerability Warning in SmarterTools SmarterMail
The Cyber Security Agency of Singapore (CSA) has issued an alert regarding a major security flaw in the SmarterTools SmarterMail email software. This vulnerability, with a CVSS score of 10.0, could be exploited to achieve remote code …
Evolution of MuddyWater: New Tools and Tactics in Cyberattacks on Israel and Egypt
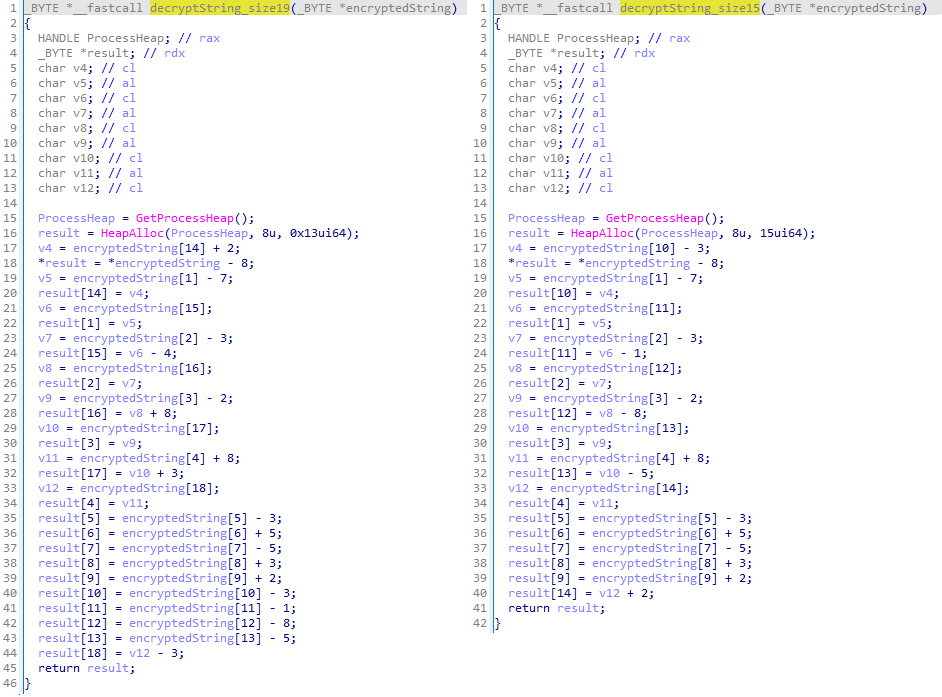
ESET researchers have discovered new activities of the Iran-aligned cyber espionage group MuddyWater (also known as Mango Sandstorm or TA450). This campaign primarily targets organizations in Israel and, in one confirmed case, Egypt, showing significant evolution in their technical and tactical …
Critical vulnerability in n8n allows remote code execution (CVE-2025-68613)

A critical security vulnerability has been revealed in the n8n workflow automation platform. The flaw, if successfully exploited, could result in arbitrary code execution under certain circumstances.
The vulnerability, tracked as CVE-2025-68613, has a CVSS score of 9.9 out of 10.0, underscoring its …
Why Third-Party Access Remains the Weak Link in Supply Chain Security

The Supply Chain: A Blind Spot in Identity Security
Security breaches often originate at the weakest link in the chain, and increasingly, this entry point is third-party access. Suppliers, contractors, and partners require access to internal systems to operate, but these permissions become …
86% Increase in Malicious Postal Services Websites during Holiday Season

The holiday shopping season has brought with it a notable increase in cyber threats targeting consumers. According to recent data, there has been an 86% increase in malicious websites impersonating postal services in the last month. This trend underscores the growing risk for consumers awaiting …
Attack Abuses Open Source Monitoring Tool for Total Remote Access

A legitimate and widely used open source server monitoring tool has been repurposed by attackers to gain complete remote control of compromised systems.
According to findings from the Ontinue Cyber Defense Center, the activity involves Nezha, a popular monitoring platform that offers …
Coupang suffers largest data breach in South Korean history

Coupang, South Korea’s leading e-commerce platform, has revealed a massive data breach affecting 33.7 million customer accounts, equivalent to nearly two-thirds of the Korean population. This incident has become the largest e-commerce security event in the country’s history and could …
DXS International Confirms Cyber-Attack Affecting NHS Supplier

DXS International, a technology supplier to England’s National Health Service (NHS), has officially confirmed a cyber-attack on its systems. The incident, which was discovered on December 14, affected the company’s office servers.
In a filing to the London Stock Exchange on December 18, …
Nissan confirms data breach after attack on Red Hat

Nissan Motor Co. Ltd. has confirmed that thousands of its customers’ information has been compromised following a data breach at its software provider Red Hat in September.
Nissan, a major automaker, reported that it was indirectly impacted by the security incident at the American company Red …
Romanian Waters confirms cyber attack, critical water operations unaffected

Romania’s national water management authority, Romanian Waters (Administrația Națională Apele Române), confirmed being the victim of a ransomware attack during the weekend of December 20, 2025.
According to the National Cybersecurity Directorate (DNSC), the incident affected approximately …
54 Individuals Indicted for Aragua Train ATM Jackpotting Scheme

The U.S. Department of Justice (DoJ) has announced the indictment of 54 individuals for their alleged involvement in an automated teller machine (ATM) “jackpotting” scheme that diverted millions of dollars. The large-scale conspiracy involved the use of Ploutus malware to force ATMs across the …
Abuse of TLS Callbacks in DLLs for Detection Evasion
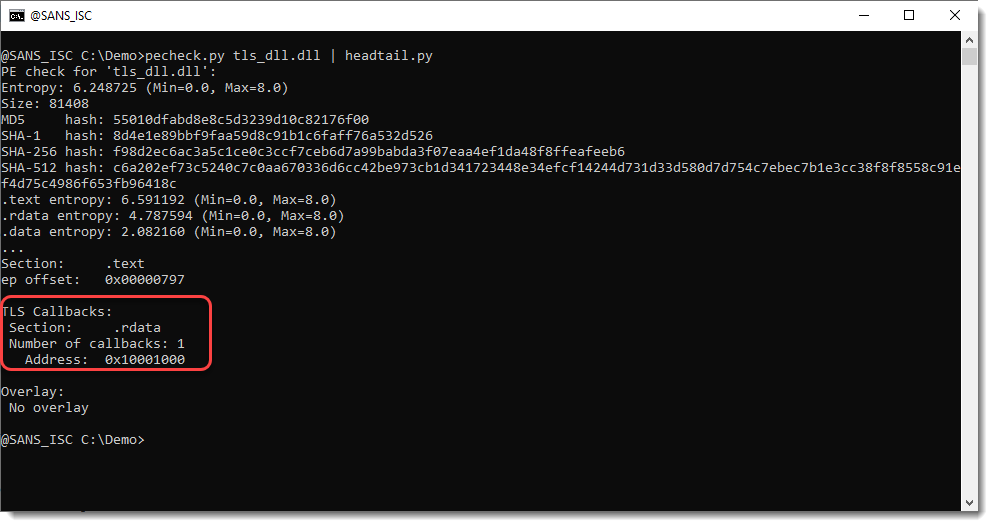
What are TLS Callbacks?
Thread Local Storage (TLS) is a Windows operating system mechanism that allows each thread in a process to have its own copy of specific variables. To support this, Windows PE (Portable Executable) executable files contain a TLS directory (IMAGE_TLS_DIRECTORY). This …
DMA vulnerability in ASRock, ASUS, GIGABYTE and MSI motherboards

A security vulnerability has been identified in specific motherboard models from leading manufacturers such as ASRock, ASUSTeK Computer, GIGABYTE and MSI. This flaw leaves systems susceptible to Direct Memory Access (DMA) attacks during the early boot phase, affecting architectures that implement …
HPE Resolves Critical Remote Code Execution Vulnerability in OneView

Hewlett Packard Enterprise (HPE) has announced the resolution of a maximum severity security vulnerability in its OneView software. The flaw, if successfully exploited, could allow remote code execution.
The critical vulnerability has been identified as CVE-2025-37164 and has a CVSS score of 10.0. …
PTA Alert: Increase in Hacking and Fraud on WhatsApp

PTA Alert on the Increase in Fraud and Hacking on WhatsApp
Pakistan Telecommunication Authority (PTA) has issued an alert to mobile users regarding the increasing number of hacking and cyber fraud incidents through WhatsApp. Scammers are using social engineering tactics to trick people into gaining …
ThreatsDay Newsletter Summary: The Constant Evolution of Attack Tactics

This week’s ThreatsDay newsletter highlights the continued adaptation of attackers, who are reconfiguring existing tools and finding new angles of attack on familiar systems. Small tactical changes are adding up quickly, suggesting possible directions for future security breaches.
Constantly …
WatchGuard fixes actively exploited critical vulnerability in Fireware OS (CVE-2025-14733)

WatchGuard has issued a security alert and released patches to address a critical vulnerability in its Fireware operating system that the company has confirmed has been actively exploited in real-world attacks. The vulnerability, identified as CVE-2025-14733, affects IKEv2 VPN configurations and …
Cisco Alerts on Critical Zero-Day Vulnerability Exploited by China APT

Cisco has issued an alert regarding a maximum severity zero-day vulnerability in its Cisco AsyncOS software. This flaw has been actively exploited by an advanced persistent threat (APT) actor with ties to China, dubbed UAT-9686, in attacks targeting Cisco Secure Email Gateway and Cisco Secure Email …
Kimsuky distributes DocSwap malware via QR codes in phishing campaign

North Korean threat group Kimsuky has been linked to a new cyberattack campaign that uses QR codes to distribute a new variant of the DocSwap Android malware. Attackers are using phishing sites that imitate South Korean logistics company CJ Logistics to trick victims.
Distribution and Deception …
DoD names ISACA as global credentialing authority for CMMC

The US Department of Defense (DoD) has designated ISACA as the global credentialing authority for the Cybersecurity Maturity Model Certification (CMMC) program. This designation seeks to ensure that defense contractors meet strict cybersecurity standards.
The CMMC program, introduced by DoD in …
Hacking group Jewelbug shifts focus to European government targets, using novel C2 infrastructure

The threat group known as Jewelbug, also tracked by Check Point Research as Ink Dragon, has intensified its attacks against government targets in Europe since July 2025. Although the actor, aligned with China and active since at least March 2023, continues to attack entities in Southeast Asia and …
Kimwolf botnet infects 1.8 million Android TV devices, uses ENS to evade detection

The Kimwolf botnet, a new distributed denial of service (DDoS) threat, has recruited a massive army of at least 1.8 million infected devices, primarily Android-based TVs, set-top boxes, and tablets. According to research by QiAnXin XLab, the botnet is associated with the infamous AISURU botnet. …
Google Patches Three Zero-Day Vulnerabilities in Chrome, One Exploited in the Wild

Google released a security update for Chrome on December 10, patching three new vulnerabilities, including a high-severity one that is being actively exploited in the wild. This vulnerability represents the eighth Chrome zero-day exploited in 2025.
The High Severity Zero-Day Vulnerability
Google …
CISA Adds WinRAR Vulnerability to KEV Catalog for Active Exploitation

CISA warns about WinRAR vulnerability
The US Cybersecurity and Infrastructure Security Agency (CISA) has added a vulnerability affecting WinRAR compression software to its catalog of Known Exploited Vulnerabilities (KEV), citing evidence of active exploitation.
The vulnerability, tracked as …
Fortinet, Ivanti and SAP Address Critical Security Flaws in Their Products

Fortinet, Ivanti, and SAP have released updates to address critical security flaws in their products. These vulnerabilities could allow authentication bypass or remote code execution if successfully exploited.
Fortinet Critical Vulnerabilities (CVE-2025-59718 and CVE-2025-59719)
Fortinet has …
AI Agent Orchestrates First Autonomous Cyberattack: Implications for SaaS Security

The GTG-1002 Attack: The First Autonomous Cyberspace Campaign
In November 2025, Anthropic revealed details of an unprecedented cyberespionage campaign, dubbed GTG-1002. This was the first time a case of an artificial intelligence (AI) agent orchestrating real-world intrusions with minimal human …
CastleLoader MaaS Used by Various Threat Actors: The Expansion of GrayBravo

Recent research has revealed the existence of four distinct threat activity groups that are leveraging a malware loader known as CastleLoader. This evidence reinforces previous assessment that the tool is offered to other cybercriminals under a malware-as-a-service (MaaS) model.
The threat actor …
More than 30 vulnerabilities discovered in IDEs with AI that allow data theft and RCE

A recent investigation has revealed more than 30 security vulnerabilities in several Integrated Development Environments (IDEs) powered by artificial intelligence (AI). These flaws, collectively called “IDEsaster”, combine prompt injection primitives with legitimate IDE features to …
Cloudflare suffers an outage that affects dozens of websites around the world

Cloudflare content delivery network (CDN) has experienced a new outage that has affected numerous websites globally. The failure, which occurred shortly before 10 a.m., coincided with a scheduled maintenance operation at the company’s data center in Detroit.
Affected Websites and Recurrence …
Hacking Groups Linked to China Quickly Exploit Critical React2Shell Vulnerability (CVE-2025-55182)

Two hacking groups linked to China have been detected weaponizing the newly disclosed vulnerability in React Server Components (RSC), known as React2Shell. The exploit was observed just hours after the existence of the flaw was made public, underscoring how quickly threat actors integrate new …
Intellexa's Predator Spyware Attacks Pakistani Lawyer; Technical Details and Vulnerabilities Revealed

A joint investigation by Amnesty International, Haaretz, Inside Story and Inside IT has revealed that the human rights lawyer from Balochistan province, Pakistan, was the target of Intellexa’s Predator spyware. This incident marks the first time that a member of civil society in Pakistan has …
Cloudflare Mitigates Largest DDoS Attack in History by AISURU Botnet

Cloudflare has announced the detection and mitigation of a distributed denial of service (DDoS) attack that peaked at 29.7 terabits per second (Tbps), the largest ever recorded by the company. The attack, lasting 69 seconds, was launched by the botnet for hire known as AISURU.
The AISURU Botnet: …
GhostFrame: The New Phishing Framework That Has Deceived More Than One Million Users

A new phishing framework called GhostFrame, built around a stealthy iframe architecture, has been linked to more than a million attacks, cybersecurity experts at Barracuda have found.
This attack kit distinguishes itself from known Phishing-as-a-Service (PhaaS) offerings by its innovative approach …
GoldFactory Launches Sophisticated Malware Attacks on Asian Banking Apps

Financially motivated cybercriminal group GoldFactory has launched a new wave of attacks targeting mobile users in Indonesia, Thailand and Vietnam. Attackers are using a government spoofing technique to distribute legitimate banking applications modified with malware.
The activity, observed since …
Silver Fox Uses False Flags to Camouflage ValleyRAT Attacks on Chinese Targets

The cybercriminal group known as Silver Fox has been identified orchestrating a “false flag” operation to imitate a Russian threat group. This tactic seeks to camouflage its attacks directed at organizations in China.
The SEO poisoning campaign uses Microsoft Teams lures to trick …
CVE-2025-12744: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection')
Vulnerability Description
CVE-2025-12744 is an OS Command Injection vulnerability found in the Automatic Bug Reporting Tool (ABRT) daemon.
Technical Details
- The ABRT daemon copies up to 12 characters from untrusted user-supplied input.
- These characters are inserted directly into a shell command: …
Microsoft Quietly Patches LNK Vulnerability Exploited Since 2017

Microsoft has quietly fixed a security vulnerability that has been exploited by multiple threat actors since 2017. The fix was included in the November 2025 Patch Tuesday updates.
The vulnerability, tracked as CVE-2025-9491 (CVSS score: 7.8/7.0), is a “misinterpretation of the Windows …
Salty2FA and Tycoon2FA: The Emergence of Hybrid Phishing and Its Implications for Detection
Phishing kits typically have distinctive signatures in their delivery methods and infrastructure, making attribution easier. However, analysts have recently observed an overlap between two phishing kits such as Salty2FA and Tycoon2FA, marking a significant change that complicates detection.
ANY.RUN …
Water Saci Threat Actor Evolves Tactics to Deploy Banking Trojan via WhatsApp

The threat actor Water Saci is evolving its tactics, now employing a sophisticated infection chain that uses HTA files and PDFs to propagate a worm. This worm deploys a banking trojan via WhatsApp, targeting users in Brazil.
- The attackers have shifted from PowerShell to a Python-based variant to …
Iranian Actors Attack Israeli Entities with New Backdoor MuddyViper and Charming Kitten Revelations

Threat actors linked to the Iranian state have launched a new series of attacks against Israeli entities in various sectors, deploying a previously undocumented backdoor known as MuddyViper. The activity has been attributed to MuddyWater (also known as Mango Sandstorm or TA450), a hacking group …
Critical Vulnerability in Avast Free Antivirus Allows Kernel-Level Privilege Escalation

Security researchers have revealed a critical vulnerability in Avast Free Antivirus that could allow attackers to gain elevated system privileges and execute malicious code with kernel-level access.
The vulnerability, tracked as CVE-2025-3500, received a high CVSS score of 8.8 and was made public …
India Mandates Preloading 'Undeletable' Cybersecurity App Sanchar Saathi on New Phones

India’s telecom ministry has issued a directive requiring major mobile device manufacturers to pre-install a government cybersecurity app, Sanchar Saathi, on all new phones sold in the country. According to reports, the application cannot be deleted or disabled by users.
The directive, issued …
Doxxing in children: Risks and protection strategies

The digital world offers many opportunities for self-expression and development, but it is also a space where disagreements can escalate quickly, and bullying, harassment and revenge are present. Doxxing is a leading form of online retaliation that can have a significant impact on the mental health …
North Korean actors intensify 'Contagious Interview' campaign on npm registry

North Korean threat actors responsible for the “Contagious Interview” campaign have flooded the npm registry with 197 additional malicious packages since last month. According to a Socket analysis, these packages have accumulated more than 31,000 downloads and are designed to distribute …
Teams Vulnerability Allows Microsoft Defender Bypass Through Guest Access

Ontinue security researchers have discovered a “cross-tenant blind spot” in Microsoft Teams that allows attackers to bypass Microsoft Defender for Office 365 protections using the guest access feature.
The problem is that when a user operates as a guest in an external tenant, their …
Vulnerability in legacy Python packages exposes PyPI supply chain to takeover attacks

Cybersecurity researchers have discovered vulnerable code in outdated Python packages that could pave the way for a supply chain compromise attack on the Python Package Index (PyPI) via a domain takeover technique.
Software supply chain security company ReversingLabs identified the vulnerability in …
Critical Vulnerability in Mattermost Allows Account Takeover (CVE-2025-12421)
Mattermost Critical Vulnerability Summary
A default configuration in Mattermost, an open source collaboration platform used by enterprises and government agencies, exposes deployments to critical Account Takeover risk. The vulnerability, identified as CVE-2025-12421, allows an attacker, via a …
Multiple London Local Authorities Face Serious Cybersecurity Incident

Multiple local authorities in London are dealing with a serious cybersecurity incident, it has recently emerged. The Royal Borough of Kensington and Chelsea (RBKC) and Westminster City Council (WCC) issued a statement saying they are responding to an incident identified on Monday morning.
The …
RomCom Uses SocGholish to Distribute Mythic Agent in Attack on Engineering Company

Threat actors linked to the RomCom group have been observed using the SocGholish JavaScript loader to deliver the Mythic Agent to a US-based civil engineering company. This event marks the first time that a RomCom payload distributed through SocGholish has been detected.
The attack has been …
Organizations expose credentials when using online code formatting tools

New research has revealed that organizations in sensitive industries, such as governments, telecommunications, and critical infrastructure, are exposing passwords and credentials by pasting them into online code formatting and validation tools such as JSONformatter and CodeBeautify.
Cybersecurity …
Critical Vulnerabilities Affect Fluent Bit

Critical Bug Discovery in Fluent Bit
Cybersecurity researchers have discovered a set of critical vulnerabilities affecting Fluent Bit, a widely used telemetry agent with more than 15 billion deployments. These flaws highlight weaknesses in essential components that organizations use to move logs, …
DeepSeek AI Generates Unsafe Code When Touching Politically Sensitive Topics, According to CrowdStrike

New research from CrowdStrike has revealed that the artificial intelligence (AI) reasoning model DeepSeek-R1 produces a significantly higher number of security vulnerabilities in response to requests containing topics considered politically sensitive by China.
The study, which assessed the impact …
Five Critical Vulnerabilities in Fluent Bit Could Compromise Cloud Infrastructures

Security researchers at Oligo Security have discovered five vulnerabilities in Fluent Bit, a lightweight, open-source telemetry agent, that could be chained together to compromise and take control of cloud infrastructures.
Fluent Bit is widely used in enterprise environments, and successful …
Iberia Airlines Customer Data Compromised via Supplier Breach

Security Alert: Iberia Airlines Reports Customer Data Breach
Iberia Airlines, part of the International Airlines Group (IAG) along with British Airways and Aer Lingus, has notified its customers about a security incident that compromised personal information. The data breach originated through an …
Sha1-Hulud: Second Wave of npm Supply Chain Attacks Reveals Sabotage Tactics

Multiple security companies have warned of a second wave of attacks affecting the npm registry, reminiscent of the Shai-Hulud attack of September 2025. This new campaign, called Sha1-Hulud, has compromised hundreds of npm packages between November 21 and 23, 2025.
According to Wiz researchers, the …
Cybercriminals Use Browser Notifications to Distribute Malware Through the Matrix Push C2 Platform

A new command and control (C2) platform called Matrix Push C2 is being used by cybercriminals to distribute malware, taking advantage of a legitimate feature of web browsers: push notifications.
According to a report by BlackFrog, this malicious platform tricks users with fake system notifications, …
Salesforce Alert on Unauthorized Access via Third Party Applications
 …
State of Supply Chain Defense: Annual Global Perspectives Report 2025

Alarming Increase in Supply Chain Gaps
According to BlueVoyant’s annual State of Supply Chain Defense: Annual Global Insights Report 2025, an overwhelming majority of organizations (97%) have been negatively impacted by a supply chain breach. This data represents a significant increase …
WhatsApp Exposes 3.5 Billion Phone Numbers Due to Enumeration Vulnerability

Potentially Historic Massive Data Leak
Austrian researchers have revealed a mass enumeration vulnerability in WhatsApp that allowed the extraction of 3.5 billion user phone numbers. This finding highlights a security flaw in the app’s “contact discovery” feature, which, lacking …
HackOnChat: WhatsApp Hacking Fraud Explained
CTM360 has identified a rapidly expanding WhatsApp account hacking campaign, internally called HackOnChat. This campaign uses a network of deceptive authentication portals and phishing pages to target users around the world.
Attackers exploit WhatsApp’s familiar web interface and employ …
7-Zip vulnerability under active exploitation
A newly disclosed security vulnerability affecting 7-Zip is being actively exploited in practice, according to an advisory issued by the United Kingdom’s NHS England Digital. The vulnerability allows remote attackers to execute arbitrary code on affected systems.
Vulnerability Details …
Dragon Breath and Phishing Campaigns Distribute Gh0st RAT to Chinese Users
The cyber threat landscape targeting Chinese-speaking users has intensified with the detection of multiple malware campaigns. Two recent reports highlight the sophistication of threat actors using the Gh0st RAT remote access trojan, a malware known for its versatility.
One of the campaigns involves …
Dragon Breath Campaign Deploys Gh0st RAT Using Sophisticated Evasion Techniques
The threat group known as Dragon Breath, also tracked as APT-Q-27 and Golden Eye, has been detected using a multi-stage loader called RONINGLOADER to deliver a modified variant of the Gh0st RAT remote access Trojan. This campaign primarily targets Chinese-speaking users and uses Trojanized NSIS …
Fortinet warns of actively exploited FortiWeb command injection vulnerability

Fortinet …
Operation WrtHug: Massive Cyberattack Compromised More Than 50,000 ASUS EoL Routers
A newly discovered cyberattack campaign, dubbed Operation WrtHug, has compromised tens of thousands of ASUS routers that are end-of-life (EoL) or outdated. The operation has recruited these devices into a vast network of botnets.
Over the past six months, SecurityScorecard’s STRIKE team …
PlushDaemon group uses new EdgeStepper backdoor for AitM attacks

The …
PlushDaemon Uses Backdoor EdgeStepper for AitM Attacks and Software Update Hijacking

The threat …
Ransomware Rise in Q3 2025: Compromised Credentials and Zero-Days Dominate

The third quarter of 2025 saw a significant increase in ransomware attacks, with an 11% increase in data breach publications compared to the previous quarter. According to a report from Beazley Security, only three ransomware groups were responsible for the majority of cases (65%), with the primary …
Does your chatbot know too much? Think twice before you tell your AI companion everything.

The idea of entering into a romantic relationship with an artificial intelligence system, popularized by the movie “Her,” has moved from the realm of science fiction to a tangible reality thanks to the proliferation of generative AI and large-scale language models (LLM). Virtual …
DoorDash Confirms Data Breach After Social Engineering Scam

Food delivery service DoorDash has confirmed that it suffered a data breach in October 2025, where some customers’ personal information was accessed. The company detailed that the incident was the result of a social engineering scam targeting one of its employees.
Details of the Data Breach …
The rise of AI in new account fraud

Artificial intelligence (AI) technology is increasingly being adopted by fraudsters to commit new account fraud (NAF) and bypass even biometric checks. This is revealed by a new report from Entrust, which analyzed data from more than one billion identity verifications in 30 sectors and 195 …
🚨 RondoDox exploits unpatched XWiki servers to expand its botnet
The RondoDox botnet malware is actively exploiting unpatched XWiki servers via the critical vulnerability CVE-2025-24893 (CVSS 9.8), allowing arbitrary remote code execution.
🔍 CVE-2025-24893
Evaluation injection bug that allows any guest user to execute remote code via the /bin/get/Main/SolrSearch …
🔎 Cybersecurity at Risk: Audit reveals critical gaps in healthcare organization
A recent cybersecurity audit revealed critical vulnerabilities in the technological infrastructure of a recognized healthcare organization.
How to Reduce Your Digital Attack Surface: Key Recommendations for Comfidentia
Key recommendations to reduce the digital attack surface in your organization.



